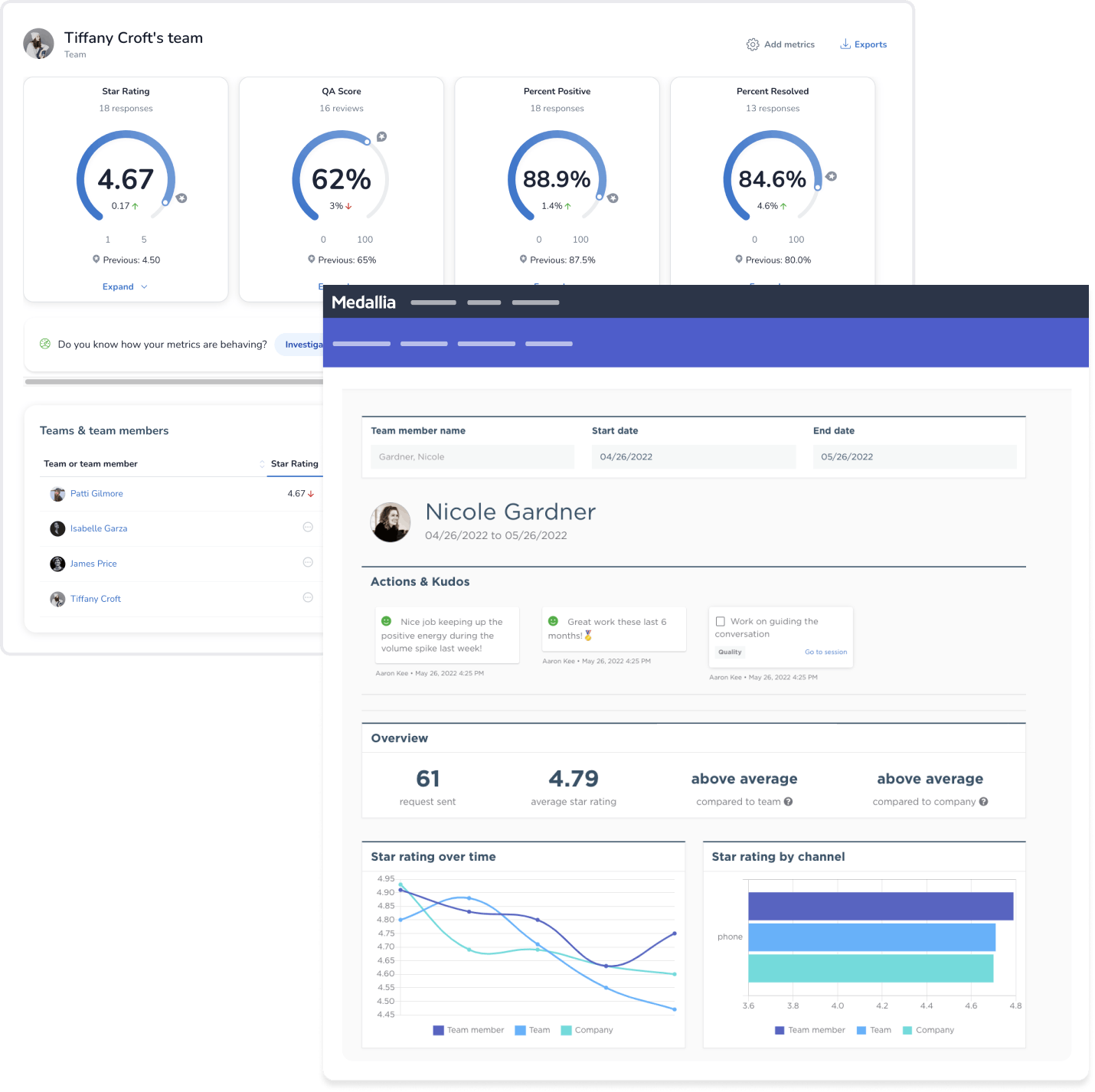
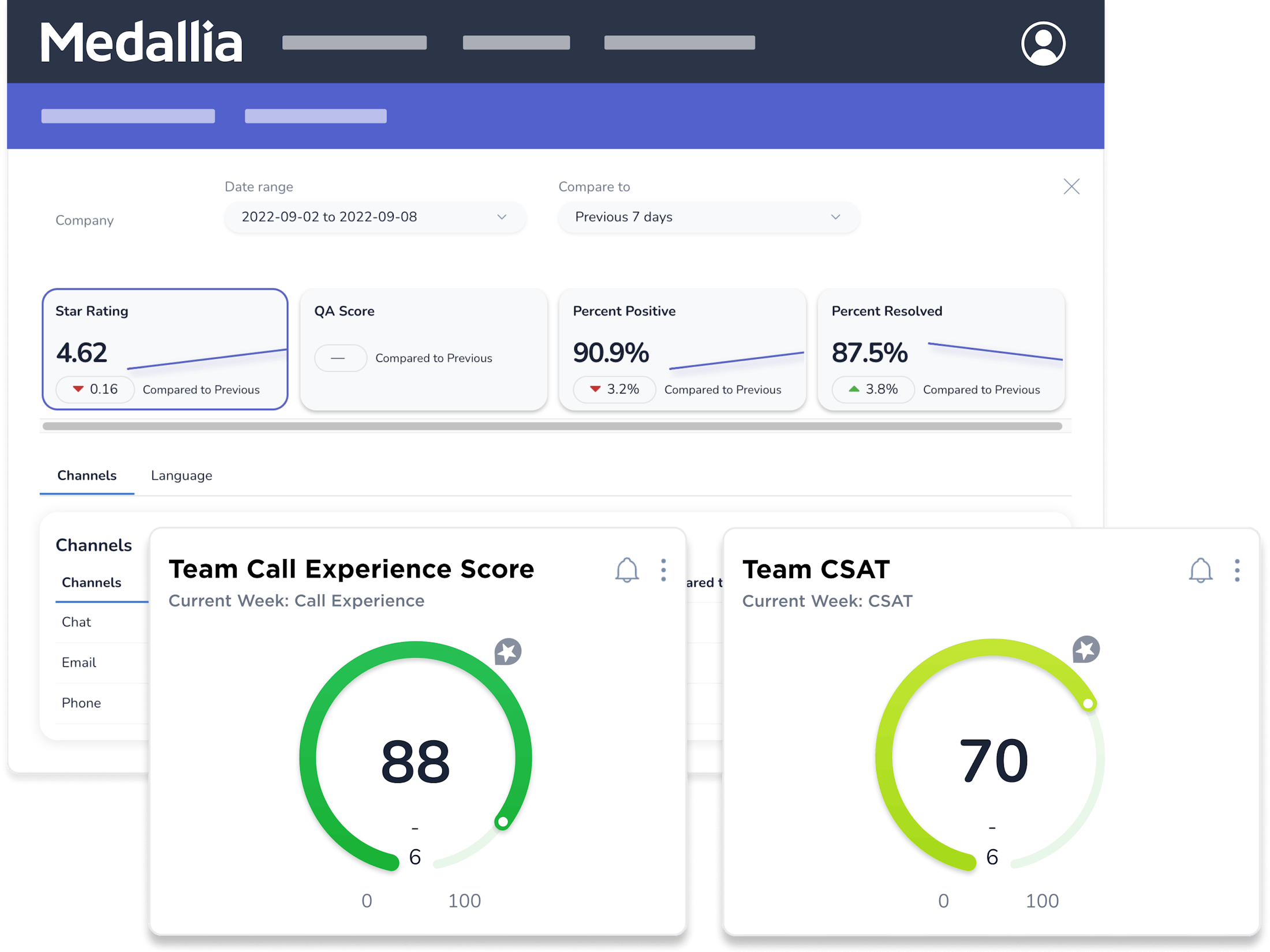
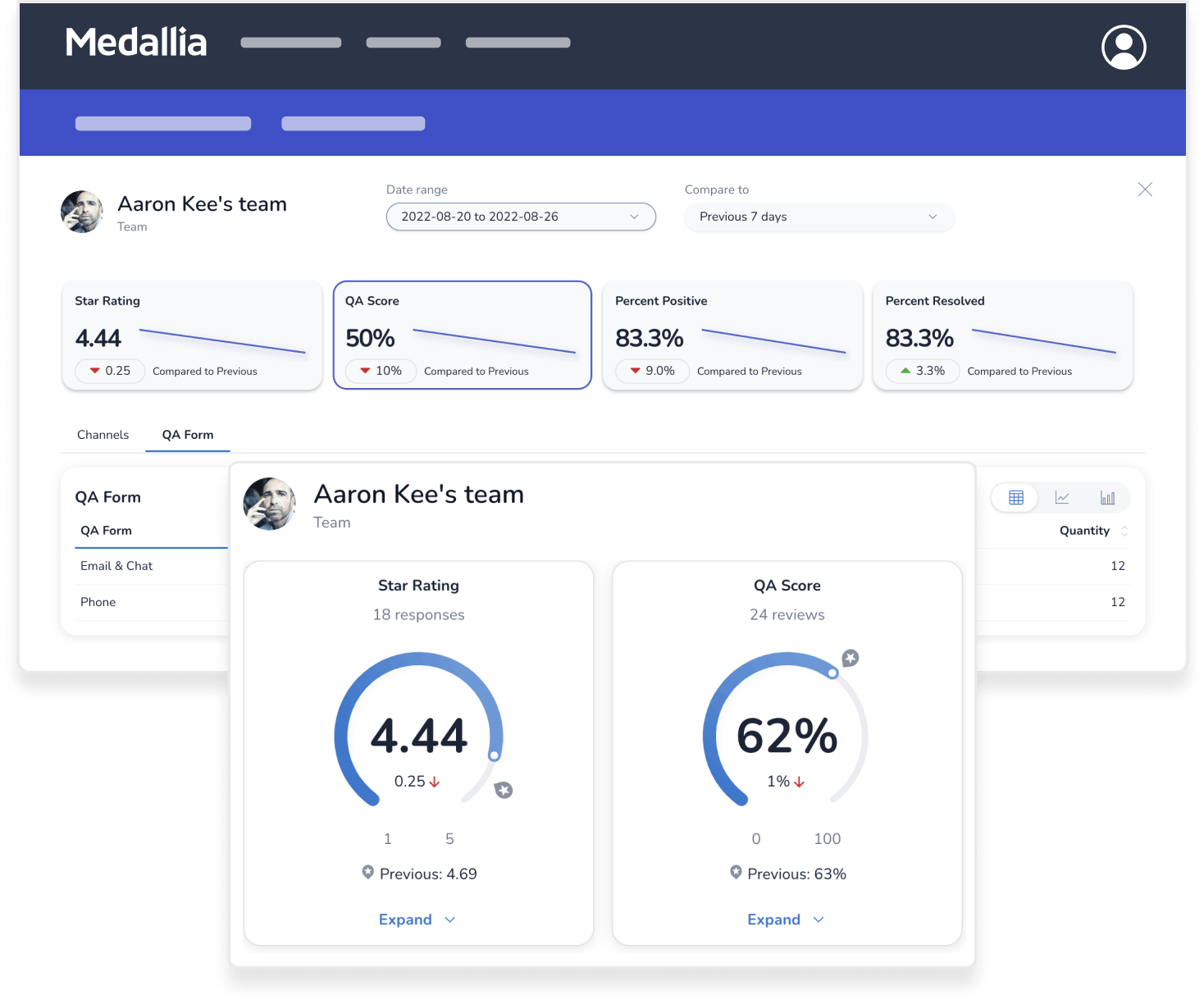
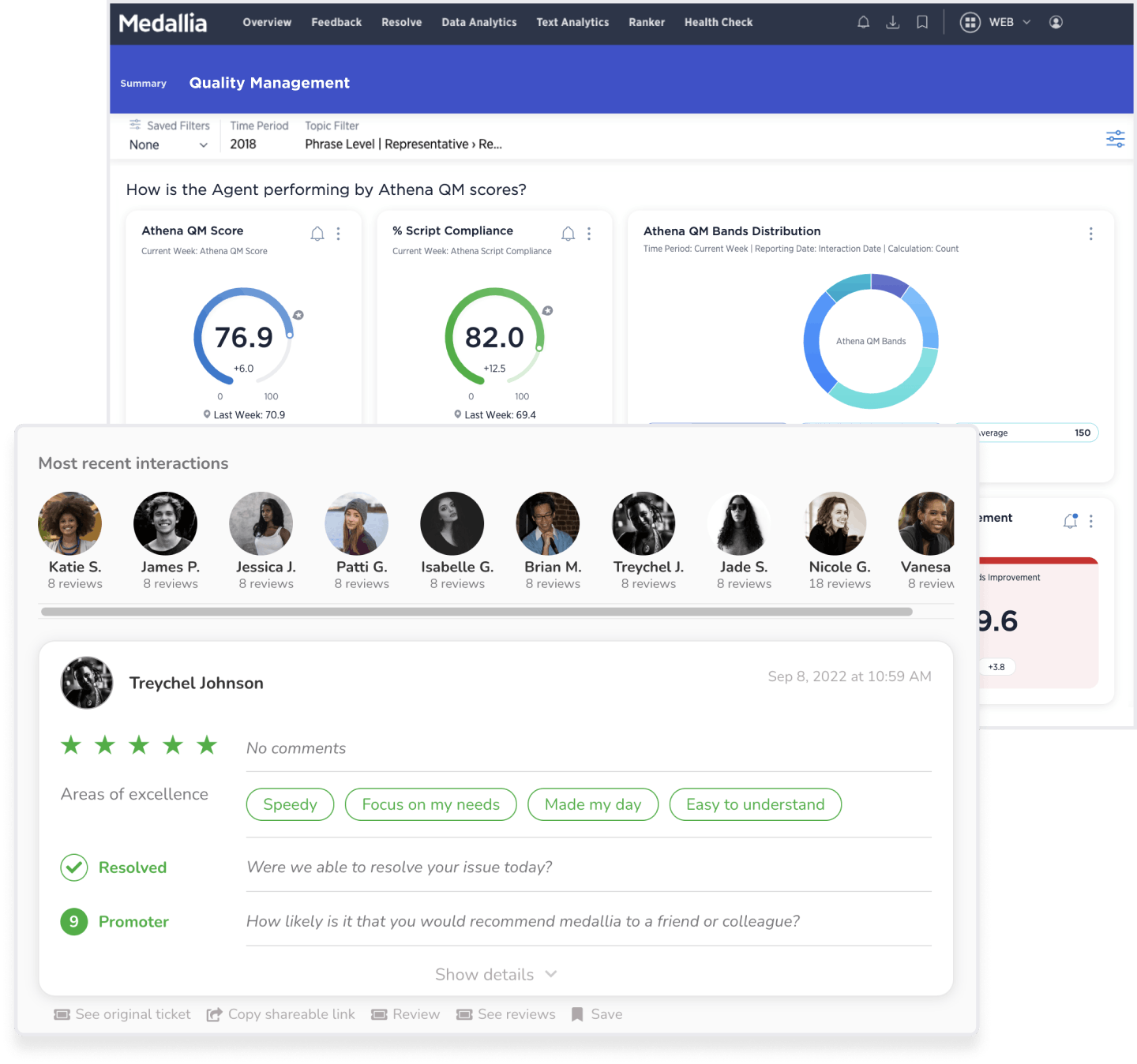
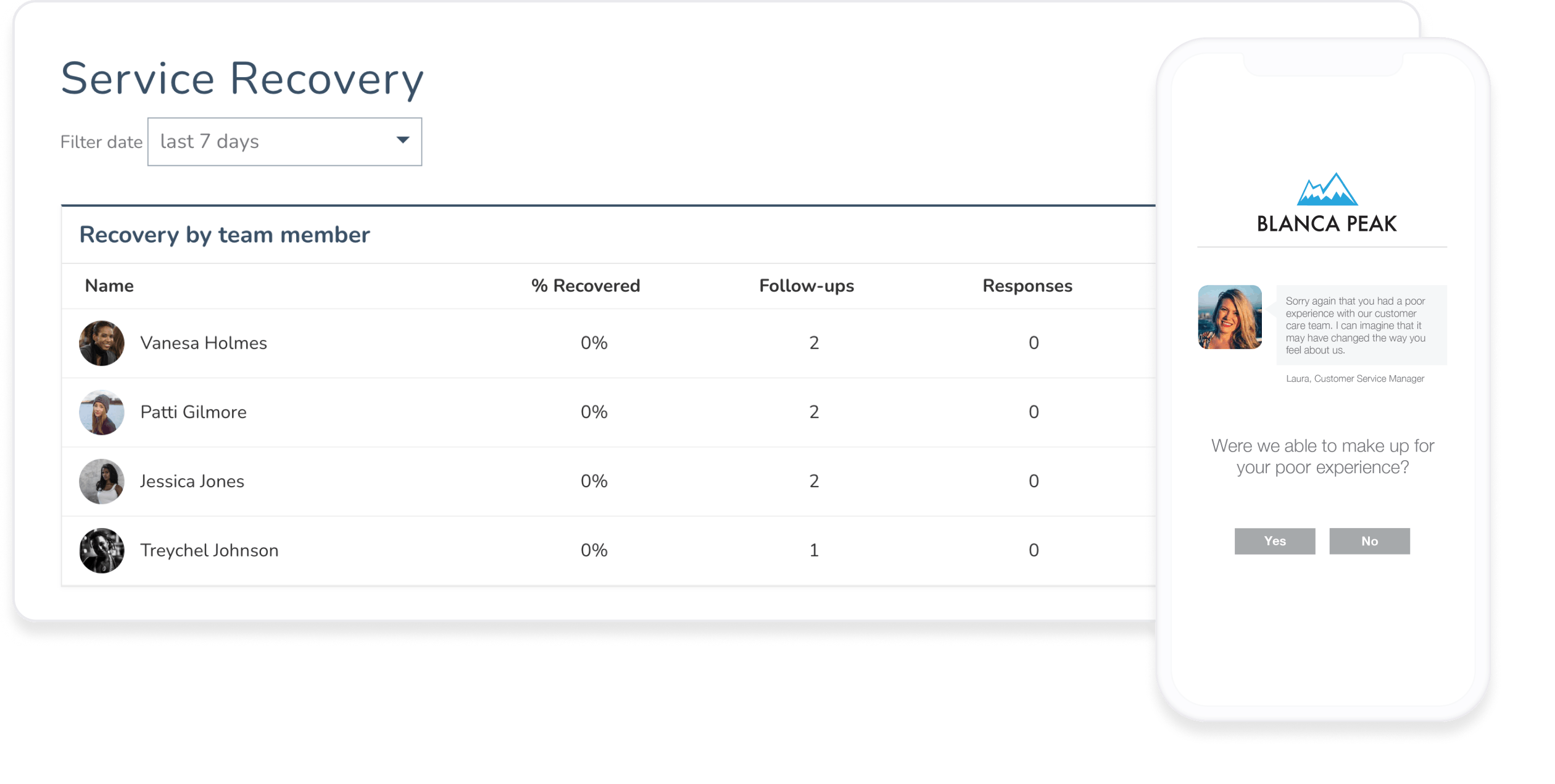
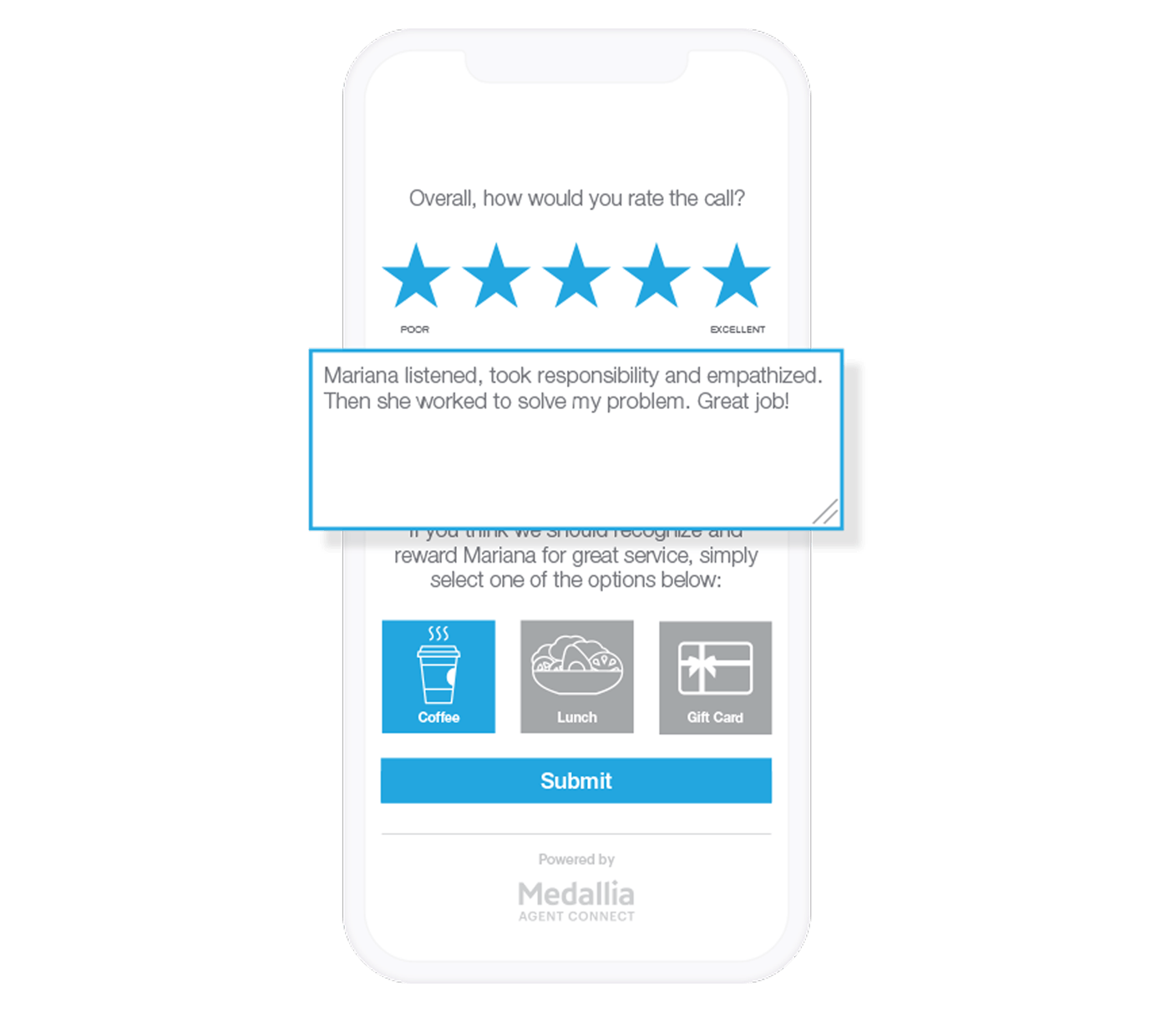
Customer service agents deal with surprises every day, but their performance should never be one of them. Keep work-from-anywhere teams connected through role-specific dashboards, transparent feedback, and personalized coaching.
Negative feedback does happen, but with Medallia’s Agent Connect you can give agents the chance to self-correct and proactively reach out for help. Put agent’s in the driver’s seat with real-time transparency.